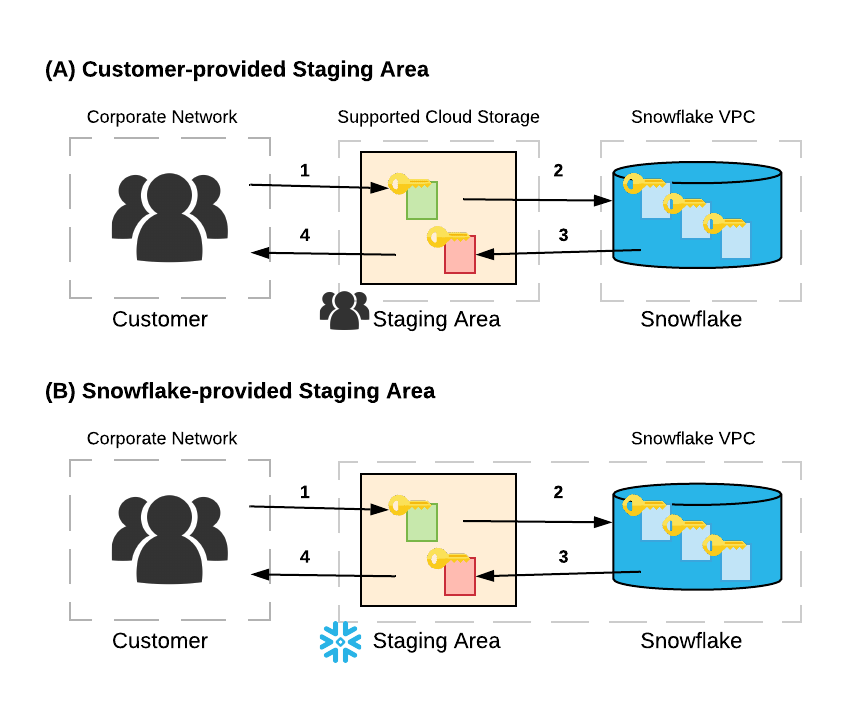
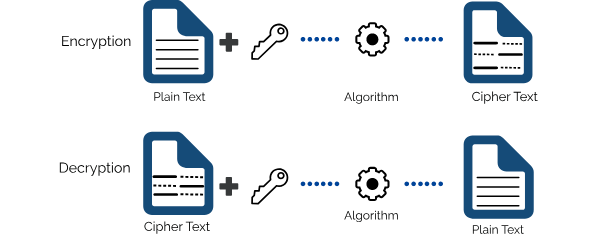
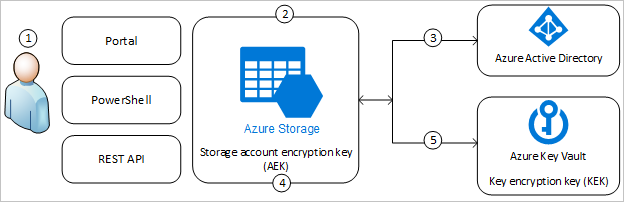
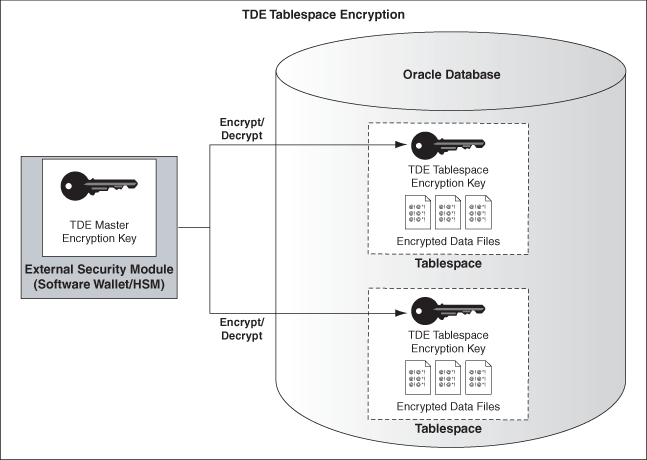
Multi-security-level cloud storage system based on improved proxy re- encryption | EURASIP Journal on Wireless Communications and Networking | Full Text
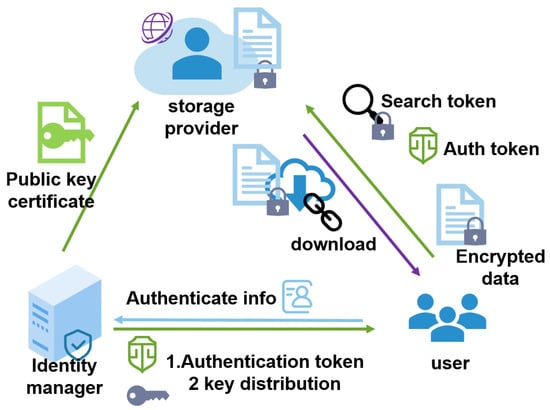
Sensors | Free Full-Text | EStore: A User-Friendly Encrypted Storage Scheme for Distributed File Systems

Secure and efficient data retrieval over encrypted data using attribute-based encryption in cloud storage | Semantic Scholar

Secure and efficient data retrieval over encrypted data using attribute-based encryption in cloud storage - ScienceDirect

Kanguru Expands Its Encrypted & Non-Encrypted Data Storage Line with New 512GB High-Capacity USB Flash Drives